Avoiding Cloud Security Breaches: 10 Best Practices That Work Today

- By Asif Ali
Gone are the days when locking the front door was enough to keep your business safe. In the cloud, there is no front door, just endless windows, open APIs, and new ways for attackers to slip in.
The rules of the game have changed. Last year alone, cloud security breaches made headlines for everyone from startups to giants, and the average breach cost hit $4.75 million. Most of these breaches started with small mistakes like a misconfigured setting, a forgotten backup, or a password that wasn’t strong enough.
You don’t need a huge budget or a team of security experts to stay safe these days. What you need is a smart, simple plan that works for the real threats out there. In this guide, we will share the cloud security best practices that really work.
Why Do Cloud Security Breaches Happen?
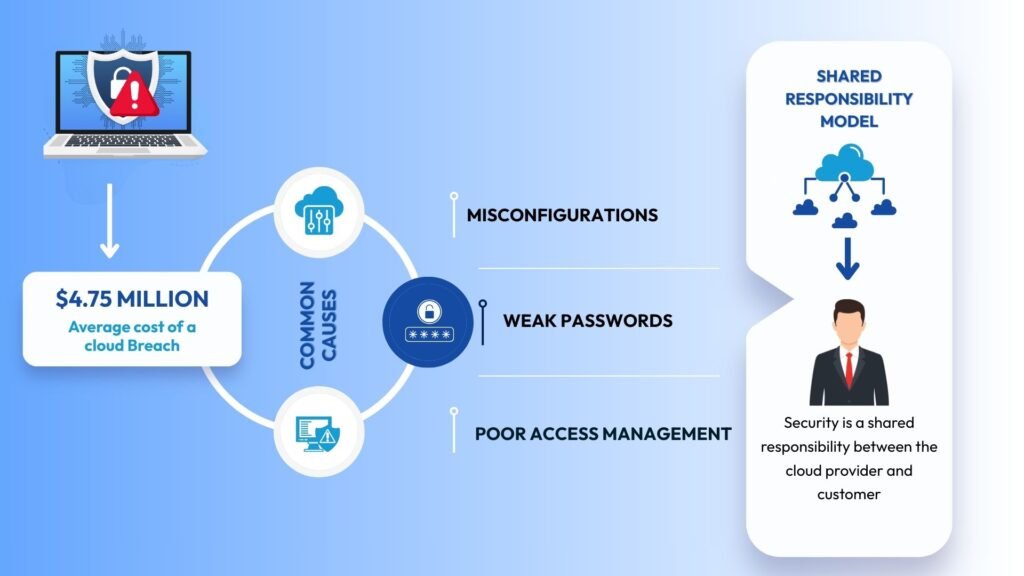
Cloud technology is brilliant, but it is easy to get tripped up. Unlike the old days when you locked the server room and called it a day, the cloud has hundreds of settings, menus, and access points. A single wrong click, a public storage bucket, a weak password, or a forgotten user account is all it takes for an attacker to get in.
Most breaches don’t happen because someone has outsmarted advanced technology, they happen because of simple missteps: a misconfigured firewall rule, an old user account left active, or sensitive data left unencrypted. These are the little cracks that cybercriminals love to exploit.
Many businesses still think cloud security is all handled by the provider. But in reality, there is a “shared responsibility model.” For example, Microsoft looks after the underlying cloud infrastructure, but you are in charge of your own data, user permissions, and application settings. If you miss something, no one is going to swoop in and fix it for you.
And cyber criminals don’t care if you are big or small. If there is a gap, they will find it. No one is too small to be a target.
Trusted Industry Frameworks for Cloud Security
So, how do you move beyond hope and guesswork? Thankfully, you don’t have to make it up as you go. The following are the trusted guides used by the world’s most secure organisations:
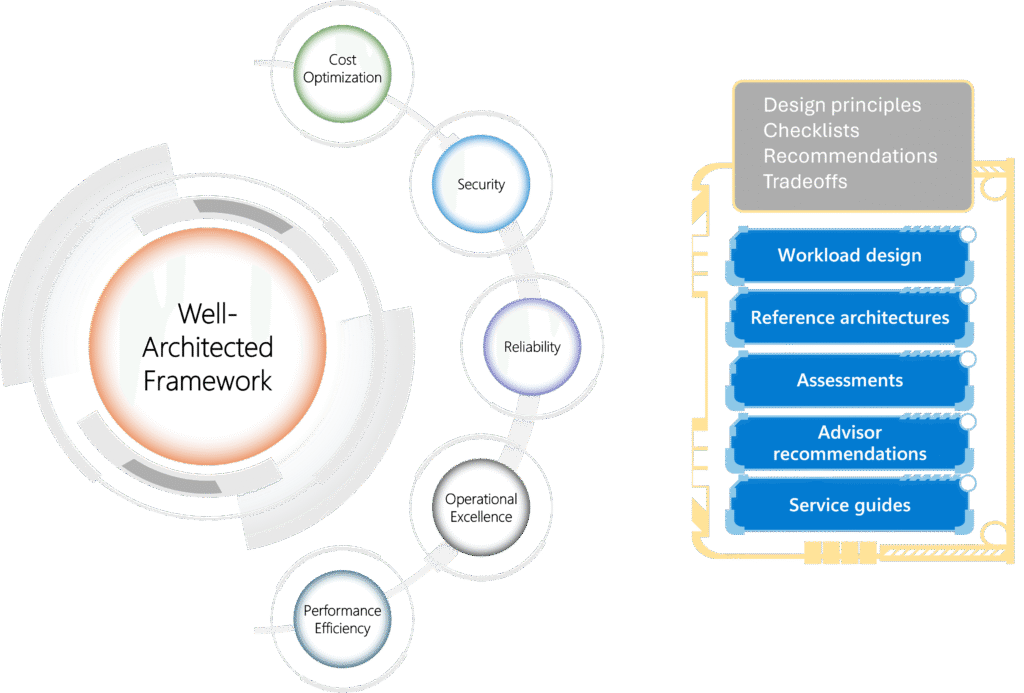
- Microsoft Azure Well-Architected Framework: Microsoft’s official set of best practices for designing, deploying, and operating secure workloads in the cloud. It covers everything from identity management to encryption and incident response.
- CIS Benchmarks: Step-by-step guides developed by global security pros. They cover secure configuration for everything, such as virtual machines, cloud storage, and containers..
- NIST Cybersecurity Framework (CSF): A comprehensive approach from the US National Institute of Standards and Technology to help organisations manage and reduce cybersecurity risks in any environment, including the cloud.
- NIST SP 800-207: Zero Trust Architecture: The blueprint for a “never trust, always verify” approach. It is about constantly checking every user, device, and request, no exceptions, no shortcuts.
How To Prevent Cloud Security Breaches – 10 Best Practices
There is no magic fix for cloud security breaches, but these ten practices come pretty close. Here is how you can protect your business from the most common breaches.
1. Enforce Least Privilege Access
It only takes one overly permissive account for things to go wrong. The best security starts with limiting what people can access. This is called “least privilege.” Everyone only gets the permissions they need for their job, nothing more.
According to the CIS Benchmarks and the Azure Well-Architected Framework, never use the root or global admin accounts for day-to-day work. Instead, set up Role-Based Access Control (RBAC) in Azure. This means assigning specific roles to users or groups like Reader, Contributor, or Billing Reader, so no one has more power than they need.
Open your cloud dashboard and look at your IAM (Identity and Access Management) roles. Determine who has access to what, remove any “just in case” permissions, and make sure every account is set up with the least privilege possible.
2. Segment Your Network
Think of your cloud like a block of flats. You wouldn’t want a burst pipe in one flat to flood the whole building. That is why network segmentation is so important.
Don’t let everything in your cloud be connected together. With tools like Azure Virtual Networks (VNets) and subnets, you can split up your cloud environment so different projects, apps, or departments are kept apart. This makes it much harder for a problem in one area, like a hacked test server, to spread to everything else.
Follow the guidance from the NIST Cybersecurity Framework and the CIS Benchmarks: separate your production, development, and testing environments. Take it a step further by dividing critical workloads (like databases and web servers) into separate subnets.
Draw a simple map of your current cloud setup. Check if everything is bundled together or if you have clear boundaries. Make sure a breach in your dev environment can’t reach your customer data in production. If you spot any weak points, now is the time to fix them.
3. Make Micro-Firewalls Your First Line of Defence
Leaving cloud resources wide open is like leaving your front door unlocked. Attackers are always scanning the internet for weak points.
That is where micro firewalls for cloud computing come in. In Azure, these are called Network Security Groups (NSGs), and in AWS, they are Security Groups. They act as digital gatekeepers and control what kind of network traffic is allowed in or out of your resources.
The best practice is to block all inbound traffic from the internet by default. Only open the specific ports and protocols that your app really needs, and only to trusted sources. For example, allow HTTPS (port 443) for your website, but only allow SSH (port 22) from your office’s IP address.
To do this, check your firewall rules for any open ports you don’t recognise, or services that don’t need to be exposed. Close anything you are not using. Every closed port is one less way for attackers to get in.
4. Encrypt Everything – At Rest, In Transit, Always
If you are not encrypting your data, you might as well be sending confidential files on a postcard. In the cloud, data needs protection whether it is sitting in storage or moving across the internet.
To do this, use encryption for everything, such as files stored in the cloud (“at rest”) and files being transferred (“in transit”). Azure, for example, encrypts data at rest by default, but you can take it further by managing your own encryption keys with Azure Key Vault or a similar tool. When data moves, make sure you are using the latest security protocols (at least TLS 1.2) for every connection.
Double-check your cloud settings. Check if all your databases, file storage, and backups are encrypted and if every website and API is using HTTPS. If not, it is time to close those gaps.
5. Automate Security Monitoring with CSPM Tools
No one has time to manually check every setting, alert, and update across a modern cloud environment. That is why Cloud Security Posture Management (CSPM) tools are a game-changer.
Put cloud-native security tools to work for you. With something like Microsoft Defender for Cloud, you can automatically scan your environment for cloud misconfiguration risks. Use features like Secure Score to see how your security posture measures up and get clear, step-by-step recommendations to fix what’s wrong.
Set up automated security scans in your cloud platform and schedule regular reviews, monthly, if not weekly. The sooner you catch a weakness, the less chance an attacker has to find it first.
6. Patch Early, Patch Often
Cyber attackers are always hunting for unpatched systems. They know just one missed update can open the door. Even in the cloud, you are still responsible for keeping your apps and operating systems up to date.
Don’t rely on memory or sticky notes. Use automated tools like Azure Automation Update Management to regularly patch your virtual machines, operating systems, and critical applications. This keeps your cloud environment protected from known vulnerabilities.
Switch on automatic patching for every system you can, and set up reports to track anything that falls behind. A well-patched cloud is a much safer cloud.
7. Log Everything And Actually Look at the Logs
When something goes wrong, the first thing you will wish for is a decent log. The truth is, logging only helps if you actually turn it on and take the time to look.
For a proper cloud log analytics setup, centralise your logs so you are not hunting around in different places for clues. Use tools like Azure Log Analytics to pull in activity, access, network flow, and error logs. Set up alerts for risky changes, like someone modifying admin privileges or deleting a critical resource.
Set alerts for the biggest risks, and make time every quarter to review your logs. It is much easier to spot a problem or prove everything is fine when you have the records in one place.
8. Adopt a Zero Trust Security Model
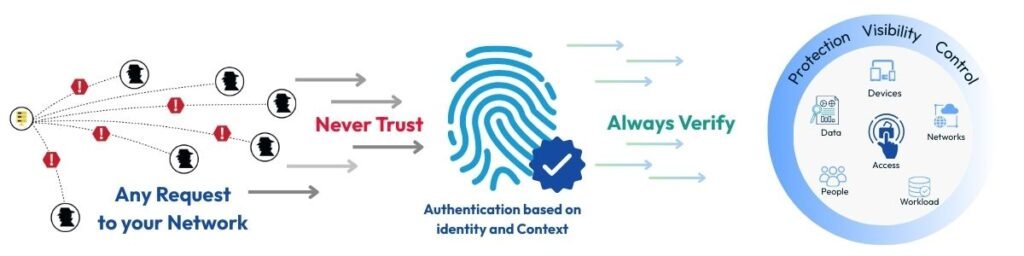
The days of trusting everything inside your network simply because it is “within” are long gone. Today’s threats come from within as much as they do from the outside. Even if someone has the right credentials or is on your internal network, they could still be an attacker in disguise.
This is exactly why Microsoft champions the Zero Trust model: “Never trust, always verify.” In this approach, the assumption is that breaches can happen at any time, so every access request, whether it is from inside or outside the network, must be continuously validated. Users, devices, and connections must prove their identity and intent before being granted access, and their status is checked at every action, not just at login.
To implement Zero Trust in your cloud environment, here is what you can do:
- Use Azure Bastion and Just-in-Time (JIT) VM Access to secure remote access and limit exposure to critical admin ports.
- Apply Identity-Aware Proxies and Conditional Access Policies to enforce strong authentication methods and ensure that only trusted devices and users can access sensitive data.
- Enable Continuous Access Evaluation, which allows real-time monitoring and re-evaluation of user sessions to ensure that trust is maintained throughout the entire duration of the session.
- Most importantly, disable public access to admin ports and apply least-privilege access controls across your entire environment.
9. Prepare for DDoS Attacks Before They Happen
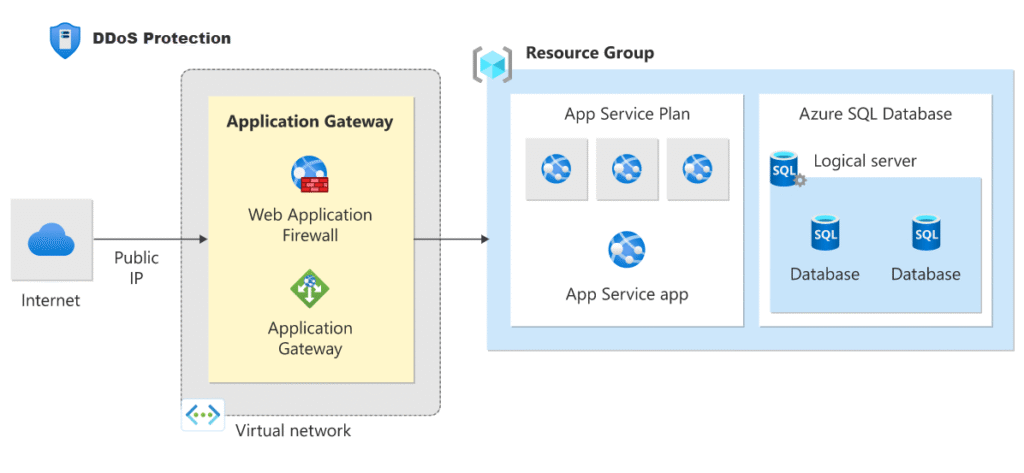
Distributed Denial-of-Service (DDoS) attacks can happen to anyone, not just the big names. All it takes is a flood of junk traffic to knock your apps offline.
To avoid this, switch on the built-in DDoS protection your cloud provider offers (Azure gives you basic coverage automatically). If you are running critical or high-traffic workloads, invest in a premium plan for better analytics and faster response.
Double-check your DDoS protection settings. Run a quick tabletop exercise with your team about what you would do if your main service were hit with a DDoS attack tomorrow.
10. Test Your Backups
It is easy to think backups have your back, but a backup you have never tested is just wishful thinking. When things go wrong, you need to know your data is safe and that you can actually get it back.
For this, automate backups for all your important data and workloads. But don’t stop there. Schedule regular restore drills (at least once a quarter) to make sure everything works as expected.
Pick a system this week and do a test restore. It is the best way to make sure your backups are more than just a box-ticking exercise.
How Mazik Global Helps You Avoid Cloud Security Breaches

At Mazik Global, security is built into everything we do, from day-to-day management to big-picture cloud strategy. Here is how we help you stay ahead of threats, keep attackers out, and meet even the toughest compliance demands.
1. Security-First Cloud Solutions
Cloud environments are constantly changing, which means your defences need to be just as dynamic. That is where our Spyglass Security Suite comes in. It is like your cloud’s 24/7 security guard. It keeps scanning, monitoring, and ready to alert you the moment something is off.
We give you live visibility into every cloud asset, and our platform continuously checks your setup against industry standards like CIS and NIST. If there is a gap, whether it is a risky misconfiguration or a new compliance rule, you will get clear guidance and a plan to fix it, fast.
But we don’t just hand you a report and walk away. Our Azure Security & Compliance Services analyze your cloud architecture deeply. We identify where attackers are most likely to strike, harden your configurations, and help you implement Zero Trust so every user, device, and app has to prove itself before getting anywhere near your data.
We also set up strong identity controls, micro-firewalls, and handle encryption so your sensitive information stays locked up tight, whether it is at rest or in transit.
2. Managed IT & Cloud Security Services
It is practically impossible for you to watch your cloud 24/7, but not for us. Our Managed Security Services take the stress out of security monitoring. With centralised logging and advanced analytics, we keep an eye on everything from unusual logins to critical file changes.
If we spot a potential breach, we jump in straight away so small issues never have a chance to become big problems. Regular vulnerability scanning and automated patch management mean your systems stay up-to-date, without you having to chase every alert.
And with our Cloud Security Posture Management, we make sure your environment stays in line with the best practices from CIS and NIST. Our tools run ongoing automated checks, flag risky settings, and offer real-time dashboards so you always know where you stand.
3. Expert-Led Security Assessments
Sometimes you just need a fresh set of expert eyes on your cloud environment. That is where our security assessments step in. At Mazik Global, we go beyond surface checks. Our specialists conduct deep cloud architecture reviews grounded in the Microsoft Well-Architected Framework, CIS Benchmarks, and NIST best practices.
We carefully map out your current security setup, look for hidden risks and potential weak spots like loose permissions to overlooked network paths. Once we have identified the gaps, we build you a clear, actionable roadmap. That way, you know exactly what to fix, in what order, and how to strengthen your defences for the long run.
4. Always-on Support
Security doesn’t take a day off, and neither do we. Mazik Global offers continuous support and ongoing security operations, so you are covered no matter when a threat might appear. Our team manages compliance monitoring, alert handling, and all the day-to-day details that keep your cloud running smoothly and safely.
But we know that true security is about empowering people, too. That is why we provide hands-on training for your IT and business teams. Since threats and standards are always evolving, we stay on top of every change to give you proactive advice and recommendations as soon as something new emerges.
Final Thoughts: Secure Your Cloud, Secure Your Future
With the recent technology, you have more control than ever to protect your data. If you follow these best practices, you will give your business the tools to grow confidently and safely.
At Mazik Global, we are here to help you put these strategies into action, avoid costly breaches, and keep your cloud environment running smoothly every single day. With the right approach, you are already one step ahead.





















